Introduction
Certification of a Device includes configuring the Device with immutable credentials that can be cryptographically verified. Device Attestation is the step of the Commissioning process whereby a Commissioner cryptographically verifies a Commissionee is in fact a certified Device. This chapter describes the Device Attestation Certificate (DAC) and the systems involved in the verification of a DAC.
The processes used to convey the DAC from a Commissionee to a Commissioner, how to verify that a Commissionee holds the private key corresponding to its DAC, and specifically how the DAC is verified are described in Section 6.2.3, “Device Attestation Procedure”.
This chapter refers to the signature algorithm ECDSA with SHA256 and to the elliptic curve secp256r1 (aka prime256v1 and NIST P-256) in compliance with the mapping for version 1.0 of the Matter Message Format of the cryptographic primitives as specified in Chapter 3, Cryptographic Primitives. Future versions of this specification might adapt these references accordingly.
Device Attestation Certificate (DAC)
All commissionable Matter Nodes SHALL include a Device Attestation Certificate (DAC) and corresponding private key, unique to that Device. The DAC is used in the Device Attestation process, as part of Commissioning a Commissionee into a Fabric. The DAC SHALL be a DER-encoded X.509v3-compliant certificate as defined in RFC 5280 and SHALL be issued by a Product Attestation Intermediate (PAI) that chains directly to an approved Product Attestation Authority (PAA), and therefore SHALL have a certification path length of 2.
The DAC also SHALL contain specific values of Vendor ID and Product ID (see Section 6.2.2.2, “Encoding of Vendor ID and Product ID in subject and issuer fields”) in its subject field to indicate the Vendor ID and Product ID provenance of the attestation certificate. See Section 6.2.3.1, “Attestation Information Validation” for how these are used.
The validity period of a DAC is determined by the vendor and MAY be set to the maximum allowed value of 99991231235959Z GeneralizedTime to indicate that the DAC has no well-defined expiration date.
-- Matter signatures are ECDSA with SHA256
MatterSignatureIdentifier ::= SEQUENCE {
algorithm OBJECT IDENTIFIER(id-x962-ecdsa-with-sha256) }
-- Matter Names
The notation used in this section to describe the specifics of the DAC uses the ASN.1 basic notation as defined in X.680. The notation below also leverages types defined in RFC 5280 such as AlgorithmIdentifier, RelativeDistinguishedName, Validity, Time, UTCTime, GeneralizedTime, or permitted extension types. Additionally, the notation below uses the ASN.1 definitions captured in the figure below:
-- The second to last RelativeDistinguishedName object in MatterDACName SEQUENCE SHALL contain an
-- attribute with type equal to matter-oid-vid and the last RelativeDistinguishedName object in the
-- SEQUENCE SHALL contain an attribute with type field set to matter-oid-pid MatterDACName ::= SEQUENCE OF RelativeDistinguishedName
-- There are two acceptable formats for MatterPA name. The first is identical to MatterDACName,
-- i.e. the second to last RelativeDistinguishedName object in MatterPAName SEQUENCE SHALL contain an
-- attribute with type equal to matter-oid-vid and the last RelativeDistinguishedName object in the
-- SEQUENCE SHALL contain an attribute with type field set to matter-oid-pid. In the second acceptable
-- format, the last element of the MatterPAName SEQUENCE SHALL be an RelativeDistinguishedName with
-- an attribute with type field set to matter-oid-vid MatterPAName ::= SEQUENCE OF RelativeDistinguishedName
-- Object definitions and references
-- X962 OIDs
id-x962 OBJECT IDENTIFIER ::= { iso(1) member-body(2) us(840) ansi-x962(10045) }
id-x962-ecdsa-with-sha256 OBJECT IDENTIFIER ::= { id-x962 signatures(4) ecdsa-with- SHA2(3) ecdsa-with-SHA256(2) }
id-x962-prime256v1 OBJECT IDENTIFIER ::= { id-x962 curves(3) prime(1) prime256v1(7) }
-- CSA and Matter specific OIDs
csa-root OBJECT IDENTIFIER ::= { iso(1) identified-organization(3) dod(6) internet(1) private(4) enterprise(1) zigbee(37244) }
-- root arc for attestation certificates
matter-att-root OBJECT IDENTIFIER ::= { csa-root 2 }
-- Matter Device Attestation Certificate DN attribute for the Vendor ID (VID) matter-oid-vid OBJECT IDENTIFIER ::= { matter-att-root 1 }
-- Matter Device Attestation Certificate DN attribute for the Product ID (PID) matter-oid-pid OBJECT IDENTIFIER ::= { matter-att-root 2 }
Device Attestation Public Key Infrastructure (PKI)
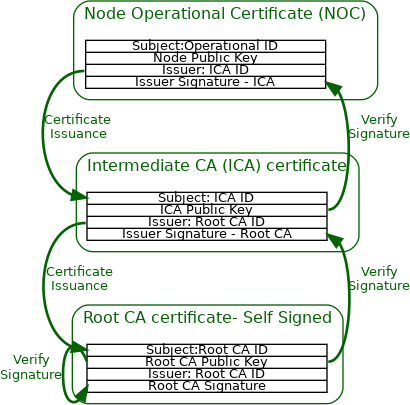
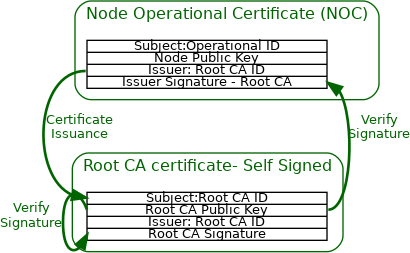
The Device Attestation PKI hierarchy consists of the PAA, PAI and individual DAC. The public key from the associated PAI certificate is used to cryptographically verify the DAC signature. The PAI certificate in turn is signed and attested to by the Product Attestation Authority (PAA) CA. The public key from the associated PAA certificate is used to cryptographically verify the PAI certificate signature. The PAA certificate is an implicitly trusted self-signed root certificate. In this way, the DAC chains up to the PAI certificate, which in turn chains up to the PAA root certificate. A PAI SHALL be assigned to a Vendor ID value. A PAI MAY further be scoped to a single ProductID value. If a PAI is used for multiple products, then it cannot be scoped to a ProductID value, otherwise the Device Attestation Procedure will fail policy validations.
Commissioners SHALL use PAA and PAI certificates to verify the authenticity of a Commissionee before proceeding with the rest of the Commissioning flow.
The subject of all DAC and PAI certificates SHALL be unique among all those issued by their issuer, as intended by RFC 5280 section 4.1.2.6, through the use of RelativeDistinguishedName s that ensure the uniqueness, such as for example a unique combination of commonName (OID 2.5.4.3), serialNumber (OID 2.5.4.5), organizationalUnitName (OID 2.5.4.11), etc. The exact additional constraints, including for the subject field, for PAA, PAI and DAC certificates, are presented in the following subsections.
The following figure shows the Device Attestation PKI hierarchy.
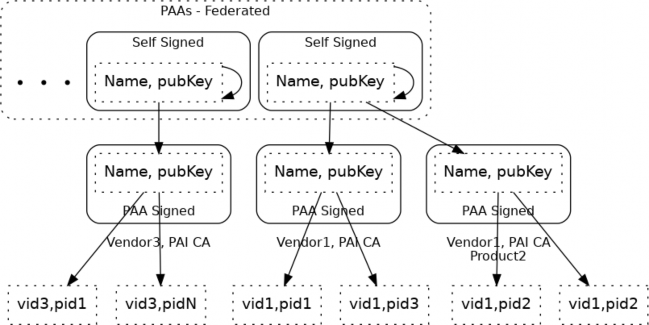
Figure 34. Device Attestation PKI hierarchy
Encoding of Vendor ID and Product ID in subject and issuer fields
The following subsections contain references to VendorID and ProductID:
Section 6.2.2.3, “Device Attestation Certificate (DAC)”
Section 6.2.2.4, “Product Attestation Intermediate (PAI) Certificate”
Section 6.2.2.5, “Product Attestation Authority (PAA) Certificate”
The values for VendorID and ProductID, where possible or required in issuer or subject fields SHALL be encoded by only one of two methods, without mixing the methods within a given field:
The "preferred method", using Matter-specific RelativeDistinguishedName attributes:
VendorID encoded as AttributeTypeAndValue entry with type equal to 1.3.6.1.4.1.37244.2.1, and value respecting encoding specified in Section 6.1.1, “Encoding of Matter-specific RDNs”.
ProductID encoded as AttributeTypeAndValue entry with type equal to 1.3.6.1.4.1.37244.2.2, and value respecting encoding specified in Section 6.1.1, “Encoding of Matter-specific RDNs”.
A "fallback method" to support certificate authorities that only allow customary RFC 5280 OIDs in the arc {joint-iso-itu-t(2) ds(5) attributeType(4)} for type values in AttributeTypeAndValue entries of RelativeDistinguishedName elements is to encode them as substrings within the commonName attribute type ({joint-iso-itu-t(2) ds(5) attributeType(4) commonName(3)}):
VendorID value encoded with substring Mvid: followed by exactly 4 uppercase hexadecimal characters without elision of leading zeroes, anywhere within the commonName, such as for example:
VendorID 0xFFF1 (65521 decimal): Mvid:FFF1
VendorID 0x2A (42 decimal): Mvid:002A
ProductID value encoded with substring Mpid: followed by exactly 4 uppercase hexadecimal characters without elision of leading zeroes, anywhere within the commonName, such as for example:
ProductID 0xC20A (49674 decimal): Mpid:C20A
ProductID 0x3A5 (933 decimal): Mpid:03A5
The "preferred method" leaves more space for content in the commonName attribute type if present. It is also less ambiguous which may allow simpler processing of certificate issuance policy validations in CAs that support the Matter-specific RelativeDistinguishedName attributes, and simplify the audit of certificates where Vendor ID and Product ID appear.
The "fallback method" is present to support less flexible CA infrastructure.
Fallback method to encode VendorID and ProductID
The "fallback method" requires exactly 9 characters that are safe to use in both PrintableString and UTF8String for either VendorID or ProductID encoding. Since these VendorID and ProductID substrings have unambiguous format, they MAY be provided anywhere within a commonName value, and therefore separator selection does not need to be considered. Note that the standard RFC 5280 length limitation for commonName attribute value is 64 characters in total (see ub-common-name in RFC 5280).
Using the "fallback method" for embedding of VendorID and ProductID in commonName in the subject field of a Device Attestation Certificate claiming VendorID 0xFFF1 and ProductID 0x00B1 can be illustrated with the following valid and invalid examples (without the double quotes):
"ACME Matter Devel DAC 5CDA9899 Mvid:FFF1 Mpid:00B1": valid and recommended since easily human-readable
"ACME Matter Devel DAC 5CDA9899 Mpid:00B1 Mvid:FFF1": valid and recommended since easily human-readable
"Mpid:00B1,ACME Matter Devel DAC 5CDA9899,Mvid:FFF1": valid example showing that order or separators are not considered at all for the overall validity of the embedded fields
"ACME Matter Devel DAC 5CDA9899 Mvid:FFF1Mpid:00B1": valid, but less readable
"Mvid:FFF1ACME Matter Devel DAC 5CDAMpid:00B19899": valid, but highly discouraged, since embedding of substrings within other substrings may be confusing to human readers.
"ACME Matter Devel DAC 5CDA9899 Mvid:FF1 Mpid:00B1": invalid, since substring following Mvid: is not exactly 4 uppercase hexadecimal digits
"ACME Matter Devel DAC 5CDA9899 Mvid:fff1 Mpid:00B1": invalid, since substring following Mvid:
is not exactly 4 uppercase hexadecimal digits
"ACME Matter Devel DAC 5CDA9899 Mvid:FFF1 Mpid:B1": invalid, since substring following Mpid: is not exactly 4 uppercase hexadecimal digits
"ACME Matter Devel DAC 5CDA9899 Mpid: Mvid:FFF1": invalid, since substring following Mpid: is not exactly 4 uppercase hexadecimal digits
If either the Vendor ID (1.3.6.1.4.1.37244.2.1) or Product ID (1.3.6.1.4.1.37244.2.2) Matter-specific OIDs appear in any RelativeDistinguishedName in the subject or issuer fields of a certificate which is part of the Device Attestation Certificate chain path, then that certificate within the chain SHALL NOT have its commonName, if present, parsed for the "fallback method", in the rest of the issuer or subject field where the Matter-specific OIDs appear. In other words, considering a field such as subject or issuer, the presence of either of these OIDs as the type for any AttributeTypeAndValue within any RelativeDistinguishedName of that field SHALL cause the "fallback method" to be skipped altogether for that field. Otherwise, when the "fallback method" can legally be used, it SHALL only be used against AttributeTypeAndValue sequences where the type field is commonName ({joint-iso-itu- t(2) ds(5) attributeType(4) commonName(3)}) in the issuer and subject fields, and any mention thereafter of using or matching a "Vendor ID" or "Product ID" with regards to a Device Attestation Procedure step SHALL rely on values obtained with that method.
For example, if a given Product Attestation Intermediate certificate has a subject field employing a particular method of encoding the VendorID and ProductID, either using only Matter-specific OIDs or only the fallback method, then it follows that a Device Attestation Certificates issued by the certificate authority of that Product Attestation Intermediate SHALL have the same DistinguishedName content in its issuer field, so that the basic path validation algorithm works. That Device Attestation Certificate MAY however have the "fallback method" used within its subject field, if the Product Attestation Intermediate certificate authority is unable to encode/reflect the Matter-specific OIDs in RelativeDistinguishedName attributes within the subject field. The rules for whether to consider the canonical or "fallback method" for VendorID and ProductID encoding applies field by field independently for each instance of subject or issuer field found in certificates within the DAC chain.
Device Attestation Certificate (DAC)
The attributes in a DAC include:

AlgorithmIdentifier, BIT STRING }
DACTBSCertificate,
Certificate ::= SEQUENCE { tbsCertificate signatureAlgorithm signatureValue

DACTBSCertificate ::= SEQUENCE {
version INTEGER ( v3(2) ),
serialNumber INTEGER,
signature MatterSignatureIdentifier,
issuer MatterPAName,
validity Validity,
subject MatterDACName, subjectPublicKeyInfo SEQUENCE {
algorithm OBJECT IDENTIFIER(id-x962-prime256v1), subjectPublicKey BIT STRING },
extensions DACExtensions }
DACExtensions ::= SEQUENCE {
basicConstraint Extension({extnID id-ce-basicConstraints, critical TRUE, extnValue BasicConstraints {cA FALSE} }),
keyUsage Extension({extnID id-ce-keyUsage, critical TRUE, extnValue KeyUsage({digitalSignature})}),
authorityKeyIdentifier Extension({extnID id-ce-authorityKeyIdentifier}), subjectKeyIdentifier Extension({extnID id-ce-subjectKeyIdentifier}), extendedKeyUsage Extension({extnID id-ce-extKeyUsage}) OPTIONAL, authorityInformationAccess Extension({extnID id-pe-authorityInfoAccess}) OPTIONAL, subjectAlternateName Extension({extnID id-ce-subjectAltName}) OPTIONAL,
}
The DAC certificate SHALL follow the following constraints layered on top of the encoding specified by RFC 5280 within the TBSCertificate structure:
The version field SHALL be set to 2 to indicate v3 certificate.
The signature field SHALL contain the identifier for signatureAlgorithm ecdsa-with-SHA256.
The issuer field SHALL be a sequence of RelativeDistinguishedName s.
The issuer field SHALL have exactly one VendorID value present.
The issuer field SHALL have exactly zero or one ProductID value present.
The subject field SHALL be a sequence of RelativeDistinguishedName s.
The subject field SHALL have exactly one VendorID value present.
The VendorID value present in the issuer field SHALL match the VendorID value found in
subject field.
The subject field SHALL have exactly one ProductID value present.
If a ProductID value was present in the issuer field, the ProductID value found in subject
field SHALL match the value found in the issuer field.
The algorithm field in subjectPublicKeyInfo field SHALL be the object identifier for prime256v1.
The certificate SHALL carry the following Extensions:
Basic Constraint extension SHALL be marked critical and have the cA field set to FALSE.
Key Usage extension SHALL be marked critical and have the KeyUsage bitstring set to
digitalSignature
Authority Key Identifier
Subject Key Identifier
The certificate MAY also carry the following additional Extensions:
Extended Key Usage
Authority Information Access
Subject Alternate Name
Valid example DAC with associated private key, in X.509 PEM format

-----BEGIN CERTIFICATE-----
MIIB6TCCAY+gAwIBAgIIDgY7dCvPvl0wCgYIKoZIzj0EAwIwRjEYMBYGA1UEAwwP TWF0dGVyIFRlc3QgUEFJMRQwEgYKKwYBBAGConwCAQwERkZGMTEUMBIGCisGAQQB
gqJ8AgIMBDgwMDAwIBcNMjEwNjI4MTQyMzQzWhgPOTk5OTEyMzEyMzU5NTlaMEsx HTAbBgNVBAMMFE1hdHRlciBUZXN0IERBQyAwMDAxMRQwEgYKKwYBBAGConwCAQwE
RkZGMTEUMBIGCisGAQQBgqJ8AgIMBDgwMDAwWTATBgcqhkjOPQIBBggqhkjOPQMB BwNCAATCJYMix9xyc3wzvu1wczeqJIW8Rnk+TVrJp1rXQ1JmyQoCjuyvJlD+cAnv
/K7L6tHyw9EkNd7C6tPZkpW/ztbDo2AwXjAMBgNVHRMBAf8EAjAAMA4GA1UdDwEB
/wQEAwIHgDAdBgNVHQ4EFgQUlsLZJJTql4XA0WcI44jxwJHqD9UwHwYDVR0jBBgw FoAUr0K3CU3r1RXsbs8zuBEVIl8yUogwCgYIKoZIzj0EAwIDSAAwRQIgX8sppA08 NabozmBlxtCdphc9xbJF7DIEkePTSTK3PhcCIQC0VpkPUgUQBFo4j3VOdxVAoESX kjGWRV5EDWgl2WEDZA==
-----END CERTIFICATE-----
-----BEGIN EC PRIVATE KEY-----
MHcCAQEEIHtcWp+0aVVH+DAQ38iXpphqmT7LfMnMD4V/kIqszwfuoAoGCCqGSM49 AwEHoUQDQgAEwiWDIsfccnN8M77tcHM3qiSFvEZ5Pk1ayada10NSZskKAo7sryZQ
/nAJ7/yuy+rR8sPRJDXewurT2ZKVv87Www==
-----END EC PRIVATE KEY-----
Human-readable contents of example DAC X.509 certificate
Certificate: Data:
Version: 3 (0x2)
Serial Number: 1010560536528535133 (0xe063b742bcfbe5d) Signature Algorithm: ecdsa-with-SHA256
Issuer: CN = Matter Test PAI, 1.3.6.1.4.1.37244.2.1 = FFF1, 1.3.6.1.4.1.37244.2.2 = 8000
Validity
Not Before: Jun 28 14:23:43 2021 GMT
Not After : Dec 31 23:59:59 9999 GMT
Subject: CN = Matter Test DAC 0001, 1.3.6.1.4.1.37244.2.1 = FFF1, 1.3.6.1.4.1.37244.2.2 = 8000
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey Public-Key: (256 bit)
pub:
04:c2:25:83:22:c7:dc:72:73:7c:33:be:ed:70:73:
37:aa:24:85:bc:46:79:3e:4d:5a:c9:a7:5a:d7:43:
52:66:c9:0a:02:8e:ec:af:26:50:fe:70:09:ef:fc:
ae:cb:ea:d1:f2:c3:d1:24:35:de:c2:ea:d3:d9:92: 95:bf:ce:d6:c3
ASN1 OID: prime256v1 NIST CURVE: P-256
X509v3 extensions:
X509v3 Basic Constraints: critical CA:FALSE
X509v3 Key Usage: critical Digital Signature
X509v3 Subject Key Identifier: 96:C2:D9:24:94:EA:97:85:C0:D1:67:08:E3:88:F1:C0:91:EA:0F:D5
X509v3 Authority Key Identifier: keyid:AF:42:B7:09:4D:EB:D5:15:EC:6E:CF:33:B8:11:15:22:5F:32:52:88
Signature Algorithm: ecdsa-with-SHA256 30:45:02:20:5f:cb:29:a4:0d:3c:35:a6:e8:ce:60:65:c6:d0:
9d:a6:17:3d:c5:b2:45:ec:32:04:91:e3:d3:49:32:b7:3e:17:
02:21:00:b4:56:99:0f:52:05:10:04:5a:38:8f:75:4e:77:15:
40:a0:44:97:92:31:96:45:5e:44:0d:68:25:d9:61:03:64

-----BEGIN CERTIFICATE-----
MIIB0DCCAXegAwIBAgIIbec9lw3wZpAwCgYIKoZIzj0EAwIwRjEYMBYGA1UEAwwP TWF0dGVyIFRlc3QgUEFJMRQwEgYKKwYBBAGConwCAQwERkZGMTEUMBIGCisGAQQB
gqJ8AgIMBDgwMDAwIBcNMjEwNjI4MTQyMzQzWhgPOTk5OTEyMzEyMzU5NTlaMDMx MTAvBgNVBAMMKE1hdHRlciBUZXN0IERBQyAwMDAxIE12aWQ6RkZGMSBNcGlkOjgw
MDAwWTATBgcqhkjOPQIBBggqhkjOPQMBBwNCAATCJYMix9xyc3wzvu1wczeqJIW8 Rnk+TVrJp1rXQ1JmyQoCjuyvJlD+cAnv/K7L6tHyw9EkNd7C6tPZkpW/ztbDo2Aw XjAMBgNVHRMBAf8EAjAAMA4GA1UdDwEB/wQEAwIHgDAdBgNVHQ4EFgQUlsLZJJTq
l4XA0WcI44jxwJHqD9UwHwYDVR0jBBgwFoAUr0K3CU3r1RXsbs8zuBEVIl8yUogw CgYIKoZIzj0EAwIDRwAwRAIgbvYsHaGRTg1JzPTB6TqfVFPABF8LCYkEP1AvV7Ah
yL4CIACKW3A6YixqtqKfkwuvw81mMVymqafU8kx5k1c0zqbe
-----END CERTIFICATE-----
Valid example DAC with associated private key, in X.509 PEM format, using "fallback method" for VendorID and ProductID in Subject
Human-readable contents of example DAC X.509 certificate, using "fallback method" for VendorID and ProductID in Subject
Certificate: Data:
Version: 3 (0x2)
Serial Number: 7919366188737521296 (0x6de73d970df06690) Signature Algorithm: ecdsa-with-SHA256
Issuer: CN = Matter Test PAI, 1.3.6.1.4.1.37244.2.1 = FFF1, 1.3.6.1.4.1.37244.2.2 = 8000
Validity
Not Before: Jun 28 14:23:43 2021 GMT
Not After : Dec 31 23:59:59 9999 GMT
Subject: CN = Matter Test DAC 0001 Mvid:FFF1 Mpid:8000 Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey Public-Key: (256 bit)
pub:
04:c2:25:83:22:c7:dc:72:73:7c:33:be:ed:70:73:
37:aa:24:85:bc:46:79:3e:4d:5a:c9:a7:5a:d7:43:
52:66:c9:0a:02:8e:ec:af:26:50:fe:70:09:ef:fc:
ae:cb:ea:d1:f2:c3:d1:24:35:de:c2:ea:d3:d9:92: 95:bf:ce:d6:c3
ASN1 OID: prime256v1 NIST CURVE: P-256
X509v3 extensions:
X509v3 Basic Constraints: critical CA:FALSE
X509v3 Key Usage: critical Digital Signature
X509v3 Subject Key Identifier: 96:C2:D9:24:94:EA:97:85:C0:D1:67:08:E3:88:F1:C0:91:EA:0F:D5
X509v3 Authority Key Identifier: keyid:AF:42:B7:09:4D:EB:D5:15:EC:6E:CF:33:B8:11:15:22:5F:32:52:88
Signature Algorithm: ecdsa-with-SHA256 30:44:02:20:6e:f6:2c:1d:a1:91:4e:0d:49:cc:f4:c1:e9:3a:
9f:54:53:c0:04:5f:0b:09:89:04:3f:50:2f:57:b0:21:c8:be:
02:20:00:8a:5b:70:3a:62:2c:6a:b6:a2:9f:93:0b:af:c3:cd:
66:31:5c:a6:a9:a7:d4:f2:4c:79:93:57:34:ce:a6:de
Product Attestation Intermediate (PAI) Certificate

AlgorithmIdentifier, BIT STRING }
PAITBSCertificate,
Certificate ::= SEQUENCE { tbsCertificate signatureAlgorithm signatureValue
The attributes in a PAI certificate include:

PAITBSCertificate ::= SEQUENCE {
version INTEGER ( v3(2) ),
serialNumber INTEGER,
signature MatterSignatureIdentifier,
issuer Name,
validity Validity,
subject MatterPAName, subjectPublicKeyInfo SEQUENCE {
algorithm OBJECT IDENTIFIER(id-x962-prime256v1), subjectPublicKey BIT STRING },
extensions PAIExtensions }
PAIExtensions ::= SEQUENCE {
basicConstraint Extension({extnID id-ce-basicConstraints, critical TRUE, extnValue BasicConstraints {cA TRUE, pathLen 0} }),
keyUsage Extension({extnID id-ce-keyUsage, critical TRUE, extnValue KeyUsage({keyCertSign}|{cRLSign})}),
authorityKeyIdentifier Extension({extnID id-ce-authorityKeyIdentifier}), subjectKeyIdentifier Extension({extnID id-ce-subjectKeyIdentifier}), extendedKeyUsage Extension({extnID id-ce-extKeyUsage}) OPTIONAL
}
The PAI certificate SHALL follow the following constraints layered on top of the encoding specified by RFC 5280 within the TBSCertificate structure:
The version field SHALL be set to 2 to indicate v3 certificate.
The signature field SHALL contain the identifier for signatureAlgorithm ecdsa-with-SHA256.
The issuer field SHALL be a sequence of RelativeDistinguishedName s.
The issuer field SHALL have exactly zero or one VendorID value present.
The subject field SHALL be a sequence of RelativeDistinguishedName s.
The subject field SHALL have exactly one VendorID value present.
If a VendorID value was present in the issuer field, the VendorID value found in subject
field SHALL match the value found in the issuer field.
The subject field SHALL have exactly zero or one ProductID value present.
The algorithm field in subjectPublicKeyInfo field SHALL be the object identifier for prime256v1.
The certificate SHALL carry the following Extensions:
Basic Constraint extension SHALL be marked critical and have the cA field set to TRUE and
pathLen field set to 0.
Key Usage extension SHALL be marked critical and have the KeyUsage bitstring set to
keyCertSign | cRLSign.
Authority Key Identifier
Subject Key Identifier
The certificate MAY also carry the following additional Extensions:
Extended Key Usage
The PAI certificate presented in the following example is for the issuer of the example DAC certificate from the previous section.

-----BEGIN CERTIFICATE-----
MIIB1DCCAXqgAwIBAgIIPmzmUJrYQM0wCgYIKoZIzj0EAwIwMDEYMBYGA1UEAwwP TWF0dGVyIFRlc3QgUEFBMRQwEgYKKwYBBAGConwCAQwERkZGMTAgFw0yMTA2Mjgx NDIzNDNaGA85OTk5MTIzMTIzNTk1OVowRjEYMBYGA1UEAwwPTWF0dGVyIFRlc3Qg UEFJMRQwEgYKKwYBBAGConwCAQwERkZGMTEUMBIGCisGAQQBgqJ8AgIMBDgwMDAw
WTATBgcqhkjOPQIBBggqhkjOPQMBBwNCAASA3fEbIo8+MfY7z1eY2hRiOuu96C7z eO6tv7GP4avOMdCO1LIGBLbMxtm1+rZOfeEMt0vgF8nsFRYFbXDyzQsio2YwZDAS BgNVHRMBAf8ECDAGAQH/AgEAMA4GA1UdDwEB/wQEAwIBBjAdBgNVHQ4EFgQUr0K3
CU3r1RXsbs8zuBEVIl8yUogwHwYDVR0jBBgwFoAUav0idx9RH+y/FkGXZxDc3DGh cX4wCgYIKoZIzj0EAwIDSAAwRQIhAJbJyM8uAYhgBdj1vHLAe3X9mldpWsSRETET i+oDPOUDAiAlVJQ75X1T1sR199I+v8/CA2zSm6Y5PsfvrYcUq3GCGQ==
-----END CERTIFICATE-----
-----BEGIN EC PRIVATE KEY-----
MHcCAQEEIEZ7LYpps1z+a9sPw2qBp9jj5F0GLffNuCJY88hAHcMYoAoGCCqGSM49 AwEHoUQDQgAEgN3xGyKPPjH2O89XmNoUYjrrvegu83jurb+xj+GrzjHQjtSyBgS2 zMbZtfq2Tn3hDLdL4BfJ7BUWBW1w8s0LIg==
-----END EC PRIVATE KEY-----
Valid example PAI with associated private key, in X.509 PEM format
Human-readable contents of example PAI X.509 certificate
Certificate: Data:
Version: 3 (0x2)
Serial Number: 4498223361705918669 (0x3e6ce6509ad840cd) Signature Algorithm: ecdsa-with-SHA256
Issuer: CN = Matter Test PAA, 1.3.6.1.4.1.37244.2.1 = FFF1
Validity
Not Before: Jun 28 14:23:43 2021 GMT
Not After : Dec 31 23:59:59 9999 GMT
Subject: CN = Matter Test PAI, 1.3.6.1.4.1.37244.2.1 = FFF1, 1.3.6.1.4.1.37244.2.2 = 8000
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey Public-Key: (256 bit)
pub:
04:80:dd:f1:1b:22:8f:3e:31:f6:3b:cf:57:98:da:
14:62:3a:eb:bd:e8:2e:f3:78:ee:ad:bf:b1:8f:e1:
ab:ce:31:d0:8e:d4:b2:06:04:b6:cc:c6:d9:b5:fa:
b6:4e:7d:e1:0c:b7:4b:e0:17:c9:ec:15:16:05:6d: 70:f2:cd:0b:22
ASN1 OID: prime256v1 NIST CURVE: P-256
X509v3 extensions:
X509v3 Basic Constraints: critical CA:TRUE, pathlen:0
X509v3 Key Usage: critical Certificate Sign, CRL Sign
X509v3 Subject Key Identifier: AF:42:B7:09:4D:EB:D5:15:EC:6E:CF:33:B8:11:15:22:5F:32:52:88
X509v3 Authority Key Identifier: keyid:6A:FD:22:77:1F:51:1F:EC:BF:16:41:97:67:10:DC:DC:31:A1:71:7E
Signature Algorithm: ecdsa-with-SHA256 30:45:02:21:00:96:c9:c8:cf:2e:01:88:60:05:d8:f5:bc:72:
c0:7b:75:fd:9a:57:69:5a:c4:91:11:31:13:8b:ea:03:3c:e5:
03:02:20:25:54:94:3b:e5:7d:53:d6:c4:75:f7:d2:3e:bf:cf:
c2:03:6c:d2:9b:a6:39:3e:c7:ef:ad:87:14:ab:71:82:19
Product Attestation Authority (PAA) Certificate

AlgorithmIdentifier, BIT STRING }
PAATBSCertificate,
Certificate ::= SEQUENCE { tbsCertificate signatureAlgorithm signatureValue
The attributes in a PAA certificate include:

PAATBSCertificate ::= SEQUENCE {
version INTEGER ( v3(2) ),
serialNumber INTEGER,
signature MatterSignatureIdentifier,
issuer Name,
validity Validity,
subject Name,
subjectPublicKeyInfo SEQUENCE {
algorithm OBJECT IDENTIFIER(id-x962-prime256v1), subjectPublicKey BIT STRING },
extensions PAAExtensions }
PAAExtensions ::= SEQUENCE {
basicConstraint Extension({extnID id-ce-basicConstraints, critical TRUE, extnValue BasicConstraints {cA TRUE, pathLen 1} }),
keyUsage Extension({extnID id-ce-keyUsage, critical TRUE, extnValue KeyUsage({keyCertSign}|{cRLSign})}),
authorityKeyIdentifier Extension({extnID id-ce-authorityKeyIdentifier}), subjectKeyIdentifier Extension({extnID id-ce-subjectKeyIdentifier}), extendedKeyUsage Extension({extnID id-ce-extKeyUsage}) OPTIONAL,
}
The PAA certificate SHALL follow the following constraints layered on top of the encoding specified by RFC 5280 within the TBSCertificate structure:
The version field SHALL be set to 2 to indicate v3 certificate.
The signature field SHALL contain the identifier for signatureAlgorithm ecdsa-with-SHA256.
The issuer field SHALL be a sequence of RelativeDistinguishedName s.
The issuer field SHALL have exactly zero or one VendorID value present.
The subject field SHALL be a sequence of RelativeDistinguishedName s.
The subject field SHALL have exactly zero or one VendorID value present.
The issuer and subject fields SHALL match exactly.
A ProductID value SHALL NOT be present in either the subject or issuer fields.
The algorithm field in subjectPublicKeyInfo field SHALL be the object identifier for prime256v1.
The certificate SHALL carry the following Extensions:
Basic Constraint extension SHALL be marked critical and have the cA field set to TRUE and have the pathLen field set to 1.
Key Usage extension SHALL be marked critical and have the KeyUsage bitstring set to
keyCertSign | cRLSign.
Authority Key Identifier
Subject Key Identifier
The certificate MAY also carry the following additional Extensions:
Extended Key Usage
The PAA certificate presented in the following example is for the issuer of the example PAI certificate from the previous section.

-----BEGIN CERTIFICATE-----
MIIBvTCCAWSgAwIBAgIITqjoMYLUHBwwCgYIKoZIzj0EAwIwMDEYMBYGA1UEAwwP TWF0dGVyIFRlc3QgUEFBMRQwEgYKKwYBBAGConwCAQwERkZGMTAgFw0yMTA2Mjgx NDIzNDNaGA85OTk5MTIzMTIzNTk1OVowMDEYMBYGA1UEAwwPTWF0dGVyIFRlc3Qg UEFBMRQwEgYKKwYBBAGConwCAQwERkZGMTBZMBMGByqGSM49AgEGCCqGSM49AwEH
A0IABLbLY3KIfyko9brIGqnZOuJDHK2p154kL2UXfvnO2TKijs0Duq9qj8oYShpQ NUKWDUU/MD8fGUIddR6Pjxqam3WjZjBkMBIGA1UdEwEB/wQIMAYBAf8CAQEwDgYD VR0PAQH/BAQDAgEGMB0GA1UdDgQWBBRq/SJ3H1Ef7L8WQZdnENzcMaFxfjAfBgNV
HSMEGDAWgBRq/SJ3H1Ef7L8WQZdnENzcMaFxfjAKBggqhkjOPQQDAgNHADBEAiBQ qoAC9NkyqaAFOPZTaK0P/8jvu8m+t9pWmDXPmqdRDgIgI7rI/g8j51RFtlM5CBpH mUkpxyqvChVI1A0DTVFLJd4=
-----END CERTIFICATE-----
-----BEGIN EC PRIVATE KEY-----
MHcCAQEEIGUSyuyuz8VD1gYjFhWXFi8BRoTFZaEpti/SjCerHMxQoAoGCCqGSM49 AwEHoUQDQgAEtstjcoh/KSj1usgaqdk64kMcranXniQvZRd++c7ZMqKOzQO6r2qP yhhKGlA1QpYNRT8wPx8ZQh11Ho+PGpqbdQ==
-----END EC PRIVATE KEY-----
Valid example PAA with associated private key, in X.509 PEM format
Human-readable contents of example PAA X.509 certificate
Certificate: Data:
Version: 3 (0x2)
Serial Number: 5668035430391749660 (0x4ea8e83182d41c1c) Signature Algorithm: ecdsa-with-SHA256
Issuer: CN = Matter Test PAA, 1.3.6.1.4.1.37244.2.1 = FFF1
Validity
Not Before: Jun 28 14:23:43 2021 GMT
Not After : Dec 31 23:59:59 9999 GMT
Subject: CN = Matter Test PAA, 1.3.6.1.4.1.37244.2.1 = FFF1
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey Public-Key: (256 bit)
pub:
04:b6:cb:63:72:88:7f:29:28:f5:ba:c8:1a:a9:d9:
3a:e2:43:1c:ad:a9:d7:9e:24:2f:65:17:7e:f9:ce:
d9:32:a2:8e:cd:03:ba:af:6a:8f:ca:18:4a:1a:50:
35:42:96:0d:45:3f:30:3f:1f:19:42:1d:75:1e:8f:
8f:1a:9a:9b:75
ASN1 OID: prime256v1 NIST CURVE: P-256
X509v3 extensions:
X509v3 Basic Constraints: critical CA:TRUE, pathlen:1
X509v3 Key Usage: critical Certificate Sign, CRL Sign
X509v3 Subject Key Identifier: 6A:FD:22:77:1F:51:1F:EC:BF:16:41:97:67:10:DC:DC:31:A1:71:7E
X509v3 Authority Key Identifier: keyid:6A:FD:22:77:1F:51:1F:EC:BF:16:41:97:67:10:DC:DC:31:A1:71:7E
Signature Algorithm: ecdsa-with-SHA256 30:44:02:20:50:aa:80:02:f4:d9:32:a9:a0:05:38:f6:53:68:
ad:0f:ff:c8:ef:bb:c9:be:b7:da:56:98:35:cf:9a:a7:51:0e:
02:20:23:ba:c8:fe:0f:23:e7:54:45:b6:53:39:08:1a:47:99:
49:29:c7:2a:af:0a:15:48:d4:0d:03:4d:51:4b:25:de
Device Attestation Procedure
The device attestation procedure SHALL be executed by Commissioners when commissioning a device. It serves to validate whether a particular device is certified for Matter compliance and that it was legitimately produced by the certified manufacturer. See Section 5.5, “Commissioning Flows” for the possible outcomes based on whether the Device Attestation Procedure succeeds or fails to attest the device.
The Device Attestation Certificate Chain MAY be read at any time, either prior to or after receipt of the AttestationResponse. The Commissionee SHALL make the Certificate Chain available whenever requested using Section 11.18.7.3, “CertificateChainRequest Command”. If the Commissioner does
not already have this information, to proceed with the validation, it SHALL request the Commissionee’s Device Attestation Certificate Chain using Section 11.18.7.3, “CertificateChainRequest Command”.
The procedure is as follows:
The Commissioner SHALL generate a random 32 byte attestation nonce using Crypto_DRBG().
The Commissioner SHALL send the AttestationNonce to the Commissionee and request Attestation Information using Section 11.18.7.1, “AttestationRequest Command”.
The Commissionee SHALL return the signed Attestation Information to the Commissioner using Section 11.18.7.2, “AttestationResponse Command”.
After execution of the procedure, the Attestation Information SHOULD be validated using the checks described in Section 6.2.3.1, “Attestation Information Validation”.
Attestation Information Validation
A Commissioner validating the Attestation Information SHOULD record sufficient information to provide detailed results of the validation outcome to users. Therefore, prior to validating Attestation Information, a Commissioner SHOULD have previously obtained the Device Attestation Certificate chain for the Commissionee, so that the DAC and PAI necessary for the procedure are available.
In order to consider a Commissionee successfully attested, a Commissioner SHALL have successfully validated at least the following:
The PAA SHALL be validated for presence in the Commissioner’s trusted root store, which SHOULD include at least the set of globally trusted PAA certificates present in the Distributed Compliance Ledger at the issuing timestamp (notBefore) of the DAC.
The DAC certificate chain SHALL be validated using the Crypto_VerifyChainDER() function, taking into account the mandatory presence of the PAI and of the PAA.
Chain validation SHALL be performed with respect to the notBefore timestamp of the DAC to ensure that the DAC was valid when it was issued. This way of validating is abided by the Crypto_VerifyChainDER() function.
Chain validation SHALL include revocation checks of the DAC, PAI and PAA, based on the Commissioner’s best understanding of revoked entities.
The VendorID value found in the subject DN of the DAC SHALL match the VendorID value in the subject DN of the PAI certificate.
If the PAA certificate contains a VendorID value in its subject DN, its value SHALL match the VendorID value in the subject DN of the PAI certificate.
The Device Attestation Signature (attestation_signature) field from Attestation Response SHALL be validated:

Success = Crypto_Verify(
publicKey = Public key from DAC,
message = Attestation Information TBS (attestation_tbs), signature = Device Attestation Signature (attestation_signature)
)
where the fields are encoded as described in Section 11.18.5.5, “Attestation Information”.
The AttestationChallenge SHALL be obtained from a CASE session, resumed CASE session, or PASE session depending on the method used to establish the secure session within which device attestation is conducted.
The AttestationNonce in Device Attestation elements SHALL match the Commissioner’s provided AttestationNonce.
The Certification Declaration signature SHALL be validated using the Crypto_Verify()
function and the public key obtained from the CSA’s Certificate Authority Certificate.
The Certification Declaration SHALL be validated:
The vendor_id field in the Certification Declaration SHALL match the VendorID attribute found in the Basic Information cluster.
The product_id_array field in the Certification Declaration SHALL contain the value of the ProductID attribute found in the Basic Information cluster.
The Certification Declaration SHALL be considered valid only if it contains both or neither of the dac_origin_vendor_id and dac_origin_product_id fields.
If the Certification Declaration has both the dac_origin_vendor_id and the dac_origin_product_id
fields, the following validation SHALL be done:
The VendorID value from the subject DN in the DAC SHALL match the dac_origin_vendor_id
field in the Certification Declaration.
The VendorID value from the subject DN in the PAI SHALL match the dac_origin_vendor_id
field in the Certification Declaration.
The ProductID value from the subject DN in the DAC SHALL match the
dac_origin_product_id field in the Certification Declaration.
The ProductID value from the subject DN in the PAI, if such a ProductID value appears, SHALL match the dac_origin_product_id field in the Certification Declaration.
If the Certification Declaration has neither the dac_origin_vendor_id nor the
dac_origin_product_id fields, the following validation SHALL be done:
The VendorID value from the subject DN in the DAC SHALL match the vendor_id field in the Certification Declaration.
The VendorID value from the subject DN in the PAI SHALL match the vendor_id field in the Certification Declaration.
The ProductID value from the subject DN in the DAC SHALL be present in the
product_id_array field in the Certification Declaration.
The ProductID value from the subject DN in the PAI, if such a Product ID is present, SHALL
match one of the values present in the product_id_array field in the Certification Declaration.
If the Certification Declaration contains the authorized_paa_list field, the following validation SHALL be done:
The Subject Key Identifier (SKI) extension value of the PAA certificate, which is the root of trust of the DAC, SHALL be present as one of the values in the authorized_paa_list field.
The certificate_id field SHOULD match the CDCertificateID field found in the entry of the DeviceSoftwareCompliance schema in the Distributed Compliance Ledger where the entry’s VendorID, Product ID and SoftwareVersion field match the respective VendorID, ProductID and SoftwareVersion attributes values found in the Basic Information Cluster.
The firmware_information field in the Attestation Information, if present, SHALL match the content of an entry in the Distributed Compliance Ledger for the specific device as explained in Section 6.3.2, “Firmware Information”. If the Commissioner does not support Firmware Information validation, it MAY skip checking this match.